Bitpixie Vulnerability Proof of Concept Unveiled
Security researchers have demonstrated a non-invasive method to bypass Microsoft BitLocker encryption on Windows devices in just five minutes without physically modifying the hardware.
The Bitpixie vulnerability (CVE-2023-21563) allows attackers with brief physical access to extract BitLocker encryption keys, potentially compromising sensitive data on corporate and consumer devices that lack pre-boot authentication.
The Bitpixie vulnerability, originally discovered in 2022 and highlighted at the Chaos Communication Congress (38C3) by security researcher Thomas Lambertz, exploits a critical flaw in Windows BitLocker encryption.
Unlike traditional hardware-based TPM sniffing attacks that require soldering skills and specialized knowledge, Bitpixie enables software-only exploitation that leaves no physical trace.
“The exploitation of the abused Bitpixie vulnerability is non-invasive, does not require any permanent device modifications and no complete disk image, thereby allowing a fast (~5 minutes) compromise,” explains researcher Marc Tanner from Compass Security.
This vulnerability specifically targets systems using BitLocker without pre-boot authentication, which is the default configuration on many Windows devices.
Linux-Based and Windows PE Exploits
Security researchers have developed two distinct exploitation methods, each with different requirements and capabilities.
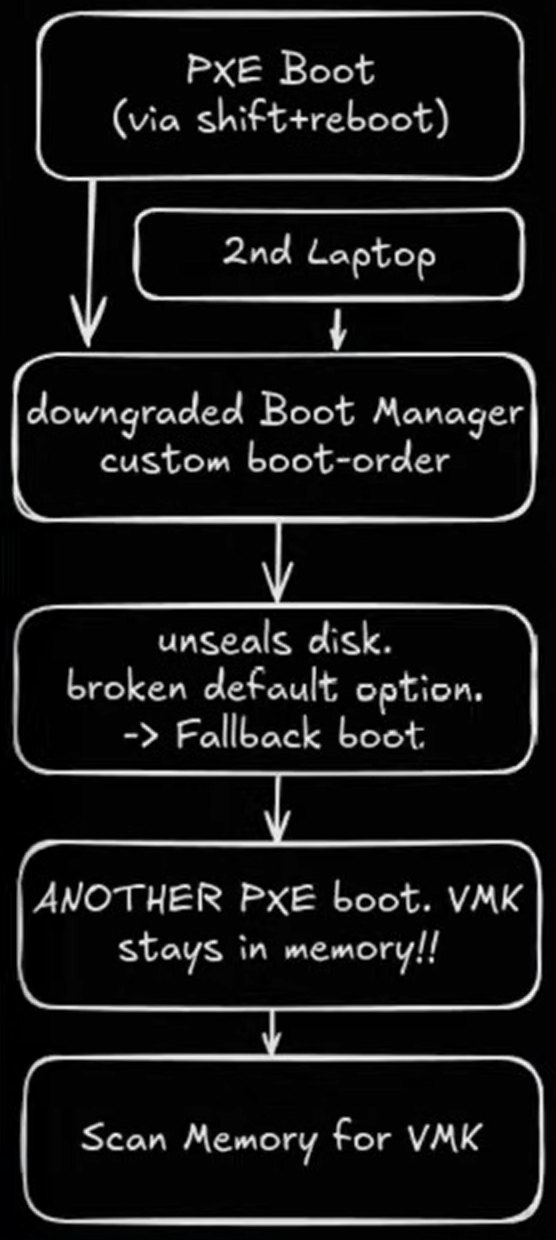
The Linux-based attack follows a multi-step process that begins by entering Windows Recovery Environment and using network boot (PXE) to load a vulnerable Windows Boot Manager.
This downgraded bootloader can then be manipulated to extract the BitLocker Volume Master Key (VMK) from system memory, effectively decrypting the entire drive.
For systems that block third-party signed components, such as Lenovo secured-core PCs, researchers created a Windows PE-based attack that relies solely on Microsoft-signed components.
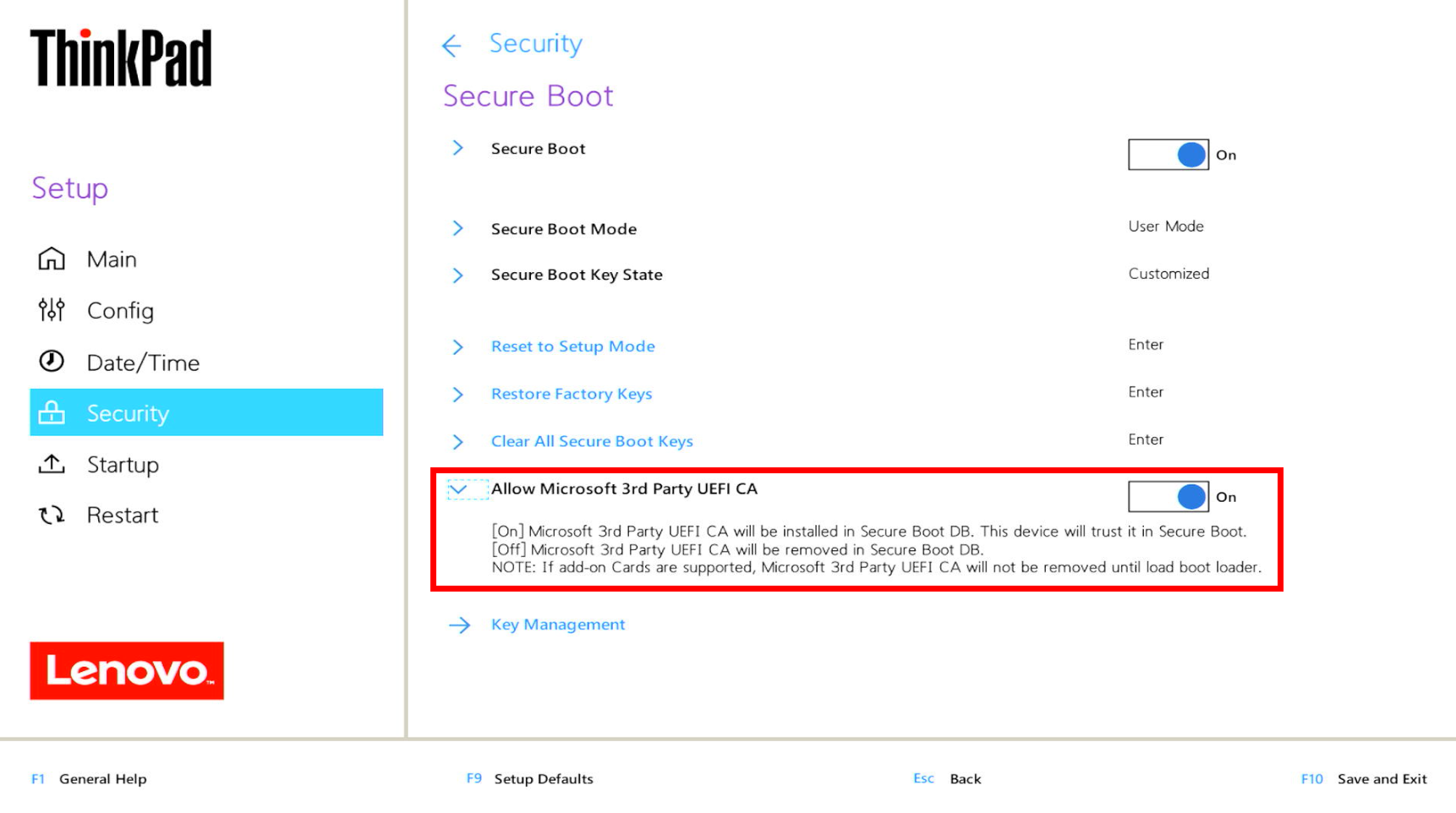
This alternative method “uses only core components signed by Microsoft” and “should therefore be applicable to all affected devices, as long as they trust the Microsoft Windows Production PCA 2011 certificate,” according to security researchers.
Both methods require only temporary physical access, a network connection, and no specialized hardware.
Protecting Against BitLocker Bypass Attacks
The fundamental flaw in BitLocker’s default configuration stems from its reliance on TPM-only protection without additional authentication factors.
“The vulnerability persists due to limitations in UEFI certificate storage, with new Secure Boot certificates not expected before 2026,” security researchers note.
Microsoft has attempted to patch the issue, but due to architectural constraints and backward compatibility requirements, the vulnerability remains exploitable through bootloader downgrade techniques.
Organizations can mitigate the risk by implementing pre-boot authentication, forcing users to enter a PIN or use a USB key before the system boots.
Microsoft security update KB5025885 also helps reduce exposure by introducing additional Secure Boot certificates and revoking older ones.
Other recommended protections include disabling network boot via BIOS/UEFI settings and implementing custom BitLocker PINs.
“The Bitpixie vulnerability – and more generally both hardware and software-based attacks – can be mitigated by forcing pre-boot authentication,” concludes the security research team, emphasizing that the default BitLocker configuration without this additional layer remains vulnerable.