Hackers Exploit AutoIT Scripts to Deploy Malware Targeting Windows Systems
Cybersecurity researchers have unearthed a sophisticated attack leveraging AutoIT, a long-standing scripting language known for its deep integration with Windows operating systems.
Often compared to .NET for its persistence in malicious campaigns, AutoIT’s simplicity and ability to interact with Windows components make it a favored tool among cybercriminals.
This weekend, a particularly intricate malware delivery mechanism was identified, featuring a double-layered AutoIT script designed to deploy a potentially devastating payload.
Multi-Layered AutoIT Malware Campaign
The attack begins with an executable named “1. Project & Profit.exe” (SHA256: b5fbae9376db12a3fcbc99e83ccad97c87fb9e23370152d1452768a3676f5aeb), a compiled AutoIT script that serves as the initial infection vector.
Upon decompilation, the script reveals a straightforward yet malicious intent.
It defines key variables pointing to suspicious URLs and local file paths, such as a download link for a secondary AutoIT interpreter saved as “C:\Users\Public\Guard.exe” and a PowerShell script, “PublicProfile.ps1,” which is generated and executed to facilitate further infection.
Additionally, another AutoIT script is retrieved and stored as “Secure.au3” in the same directory, hinting at a multi-stage deployment strategy.
The malware ensures persistence by creating a .url file in the Windows Startup directory, which triggers a JavaScript file to re-execute the AutoIT interpreter with a second-layer script named “G.”
From Executable to C2 Communication
Delving into the second layer, the “G” script stands out for its obfuscation techniques.
Strings within the code are encoded using a custom function dubbed “Wales,” which transforms ASCII values into a readable format only after decoding with a specific key.
A Python implementation of the Wales function reveals hidden references, such as checks for antivirus processes like “avastui.exe,” suggesting an attempt to evade detection.
This obfuscation underscores the attackers’ efforts to conceal their true intentions while interacting with system processes.
The attack culminates in the execution of “jsc.exe,” a legitimate Windows component, which is hijacked to load a malicious DLL named “Urshqbgpm.dll.”

This final payload is injected into the process, enabling covert operations on the compromised system.
Further analysis of the DLL reveals strong ties to AsyncRAT, a notorious remote access trojan, as evidenced by attempted connections to a command-and-control (C2) server at 139[.]99[.]188[.]124 on port 56001, a known indicator of AsyncRAT activity.
Intriguingly, the DLL also contains numerous references to PureHVNC, a lesser-known but equally dangerous framework often associated with hidden virtual network computing capabilities, allowing attackers to gain Graphical User Interface access to victims’ machines remotely.
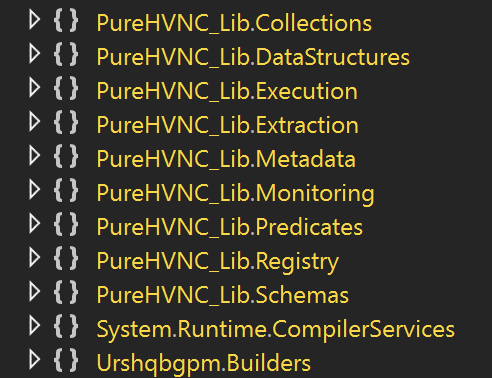
While the exact nature of the malware remains under investigation, the combination of these elements points to a highly targeted and persistent threat designed to maintain long-term access to infected systems.
This incident highlights the enduring appeal of AutoIT in the malware landscape, as its ability to blend seamlessly with legitimate Windows processes continues to challenge detection mechanisms.
Cybersecurity professionals are urged to remain vigilant, monitor for suspicious AutoIT executables, and scrutinize network traffic for connections to known malicious IPs.
As attackers refine their multi-layered approaches, understanding and mitigating such threats becomes paramount to safeguarding Windows environments from compromise.