Phishing Scams on the Rise with Sophisticated PhaaS Toolkits and Realistic Fake Pages
Cybersecurity experts are raising alarms over the proliferation of increasingly sophisticated phishing techniques that leverage dedicated Phishing-as-a-Service (PhaaS) toolkits to create authentic-looking pages.
These advanced tools allow even technically inexperienced attackers to generate convincing replicas of legitimate websites in real-time, significantly enhancing the effectiveness of credential-harvesting campaigns.
Phishing remains one of the most persistent cybersecurity threats in the digital landscape.
While the ultimate goal-stealing login credentials and sensitive information-hasn’t changed, the methods employed by attackers continue to evolve at a concerning pace.
The emergence of dynamically generated phishing pages represents a significant advancement in these malicious techniques.
Unlike traditional phishing that required manually cloning target websites, modern PhaaS toolkits automate the process, enabling attackers to spin up convincing replicas instantaneously.
LogoKit, a notorious example of such toolsets that first surfaced in 2021, continues to be actively utilized in phishing campaigns worldwide.
Dynamic Phishing Attacks Unfold
The attack typically begins with a deceptive email designed to create urgency or curiosity, compelling recipients to click without careful consideration.
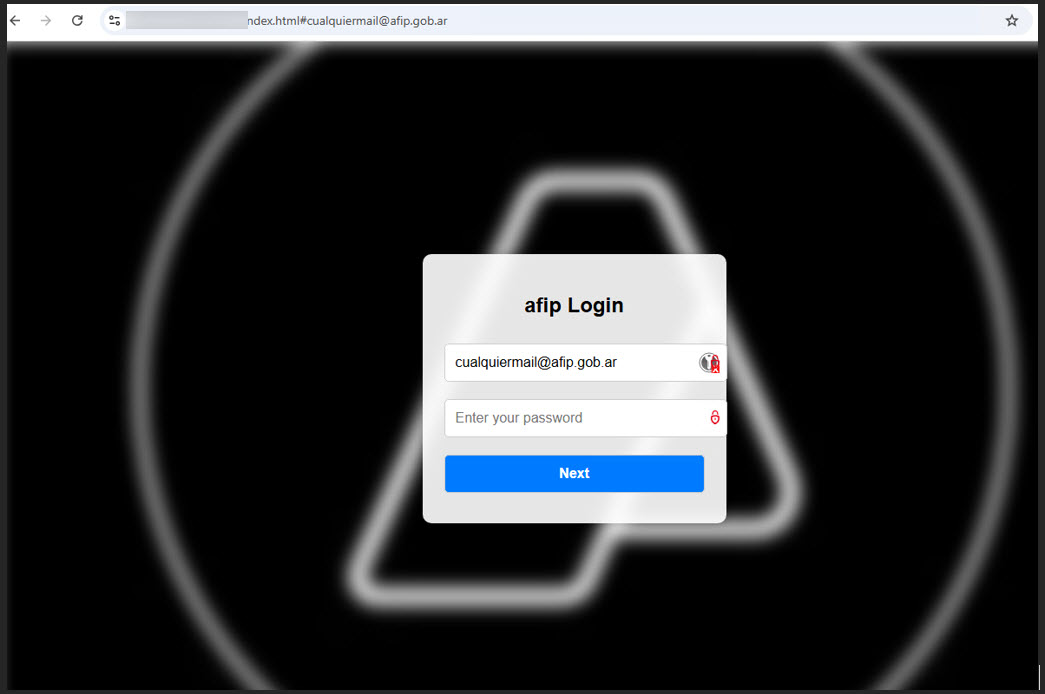
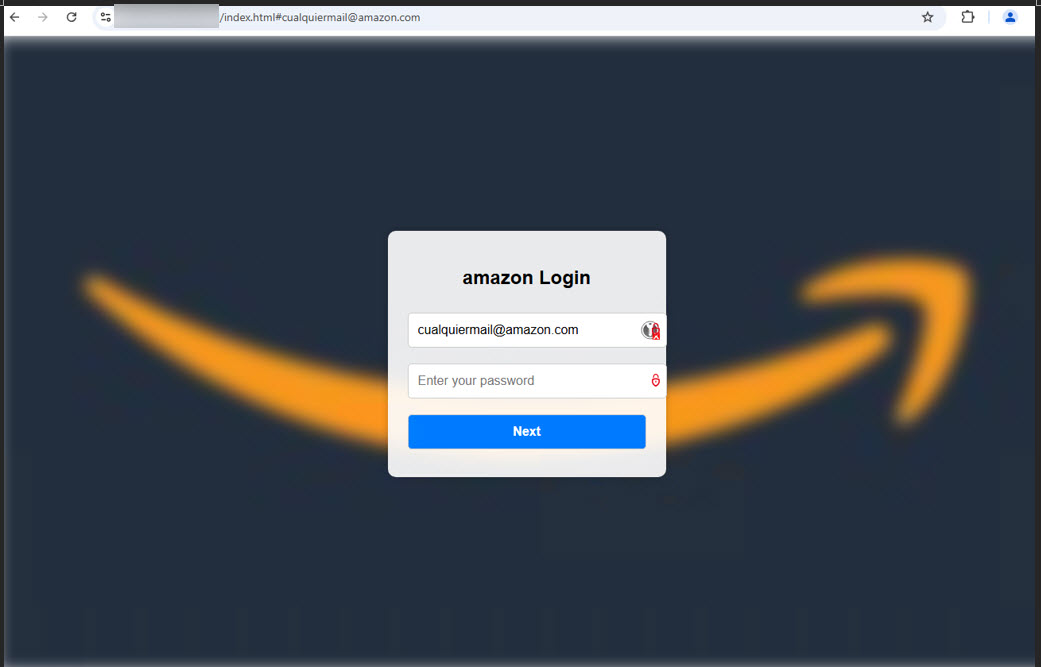
Once clicked, victims are directed to a sophisticated credential-harvesting site that dynamically retrieves branding elements of the impersonated company.
These malicious pages leverage legitimate third-party marketing services like Clearbit through their APIs to fetch corporate logos and visual identifiers in real-time.
This technique creates a convincing façade that can fool even cautious users. Adding to the deception, attackers often pre-populate fields with the victim’s email address or name, creating the illusion that the user has previously visited the site.
When victims enter their credentials, the information is immediately transmitted to attackers via AJAX POST requests.
The page then redirects to the legitimate website, leaving victims unaware that their sensitive information has been compromised.
The PhaaS model provides several significant benefits for cybercriminals.
The real-time customization capabilities allow attackers to tailor phishing pages instantly for any target organization.
By incorporating authentic visual elements, these attacks more effectively evade detection by both human users and automated security systems.
The infrastructure supporting these campaigns is typically lightweight and easily deployed across various cloud platforms, including Firebase, Oracle Cloud, and GitHub.
This agility makes the attacks both scalable and difficult for security teams to identify and neutralize quickly.
Perhaps most concerning is the democratization of these attack capabilities.
PhaaS toolkits are readily available on underground forums, lowering the technical barrier to entry and enabling even novice attackers to launch sophisticated phishing campaigns.
Protective Measures Against Advanced Phishing
Defending against these evolving threats requires a multi-layered approach combining user awareness and robust technical controls.
Security experts recommend verifying communications independently rather than clicking embedded links in suspicious messages.
Users should navigate directly to legitimate websites or contact organizations through trusted channels.
Implementing strong, unique passwords for all online accounts remains essential, especially when combined with two-factor authentication (2FA).
Security professionals particularly recommend app-based or hardware token 2FA options over SMS codes for enhanced protection.
Comprehensive security solutions with advanced anti-phishing capabilities provide another critical layer of defense against these sophisticated attacks.
The emergence of AI-enhanced phishing presents additional challenges, potentially enabling hyper-personalized scams that move beyond templated approaches.
As phishing techniques continue to evolve, maintaining vigilant awareness coupled with strong technical safeguards remains the most effective strategy for protection against these ever-morphing threats.